Tables For Ophcrack Windows 7
When I launch Ophcrack Live CD on the computer, it boots up and says “No Tables Found”. However, when I look at the contents of the CD, tables are there. Any suggestions?Ophcrack is a free Linux Live CD that cracks Windows login passwords by using LM/NT hashes through rainbow tables.
The most common issue you may experience with Ophcrack is “Tables not found” or “No tables found”. In this tutorial we’ll show you how to manually install rainbow tables into Ophcrack Live CD.Tips: A rainbow table is just a large database of precomputed hashes for a comprehensive set of passwords. But there are no guarantees Ophcrack will find a match for your password.Ophcrack No Tables Found? How to Install?Before getting started, browse to the Ophcrack Live CD you created and check if the “tables” directory is empty. If it’s empty, you need to from Ophcrack website. Unzip it and copy the contents to a USB thumb drive.
Follow these steps to install rainbow tables into Ophcrack:. When you see the warning “ No tables found“, press Enter key as the screen indicates. Select “ Ophcrack (Run Ophcrack QT graphical interface)” from the options that come up, and press OK. When Ophcrack launches, click on the Tables button in the toobar. In the popup window, you might see no tables are installed.
Click the Install button at the bottom. Browse to the rainbow table directory located in your CD or the USB thumb drive, and then click the Choose button. In the Table Selection dialog, you should see your table was installed on disk. Click OK.
Now you can load the SAM hive into Ophcrack, and click the Crack button to recover your password.
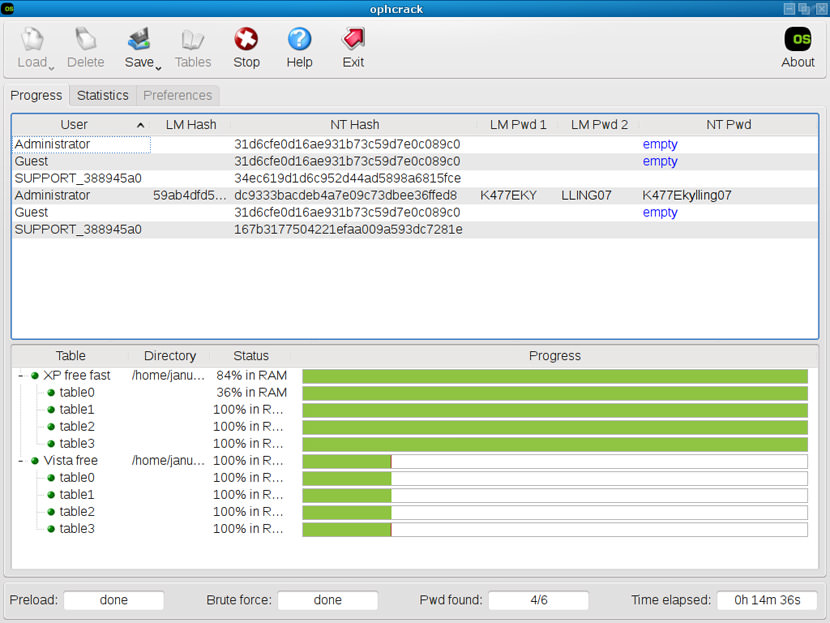
With more and more people using Vista and Win7, I decided it was time to get my NT hash cracking on. So, I installed Windows 7 in a VM, setup up some lame test accounts:Username:PasswordTest:sevenlame:lamelamepass:lamepassyourmom:yourmom18j4:18j4I then ran it through Ophcrack. What came up?
Nothing but 'lame' and 'l8j4' and they were only found because Ophcrack bruteforces from 1-4 characters. I was quite surprised that the other passwords couldn't be found. I know Ophcrack exploits the weak LM hash used in XP and preceding, while the Vista Free tables are based on a dictionary and mutations, but I still figured that it would find all of those lame passwords. Yet, it didn't.I was just wondering, if any of you have cracked some NT hashes, be it from Vista or Windows 7, did you use Ophcrack?
What was the password? What tables did you use? And, how long did it take?If you use something other than Ophcrack (JTR, Cain, etc.), what do you use? What tables do you use and how large are they? On average, how long does it take you to crack an NT hash?
With more and more people using Vista and Win7, I decided it was time to get my NT hash cracking on. So, I installed Windows 7 in a VM, setup up some lame test accounts:Username:PasswordTest:sevenlame:lamelamepass:lamepassyourmom:yourmom18j4:18j4I then ran it through Ophcrack. What came up? Nothing but 'lame' and 'l8j4' and they were only found because Ophcrack bruteforces from 1-4 characters. I was quite surprised that the other passwords couldn't be found. I know Ophcrack exploits the weak LM hash used in XP and preceding, while the Vista Free tables are based on a dictionary and mutations, but I still figured that it would find all of those lame passwords. Yet, it didn't.I was just wondering, if any of you have cracked some NT hashes, be it from Vista or Windows 7, did you use Ophcrack?
What was the password? What tables did you use? And, how long did it take?If you use something other than Ophcrack (JTR, Cain, etc.), what do you use? What tables do you use and how large are they? On average, how long does it take you to crack an NT hash?I haven't had any luck with the Vista one, either. Rainbow tables are a waste of time and space when it comes to getting into a Windows box, unless you're trying to access encrypted files. If you have access to the machine, it's yours in less than 5 minutes.So how would one go about this?
Tables For Ophcrack Windows 7 Usb
Keep in mind that in my case these are customer machines. All too often the during the intake process the non-technical office manager forgets to ask for the password. We trying calling the customer first, but sometimes you get one that doesn't call back for days (vacation, whatever). It would be nice if I could get the PW as easy as removing it.
No-one really said why they were cracking Windows boxes, I was just thinking about removing the password, which is easy as pie. Gotta do what you gotta do, right? Besides, if you back up the SAM, you can set the password to nothing, do what you need to do, then put the old SAM back and the original password will be reinstated.blink blink.
Ophcrack Vista 7
Oooohhhhh! What a novel idea.Never thought of that. In my case I didn't need to, though. Just let 'em know we removed it to do our work.Every once in a while I get the 'you can do that?!'